Are the programmes we run secure? Will the software that is in the process of development be secure? The only certainty we have is that all software can contain weaknesses or vulnerabilities. These cracks can allow a person with unwanted intentions to gain access to the program. He or she could, for example, malfunction it or obtain confidential information. Vulnerability detection is now presented as a key tool to assess the most appropriate solution(s) and prevent future incidents.
“The formulation of a problem is more important than its solution”
Albert Einstein
Many of these vulnerabilities are easy to detect by the developer himself, but others are more difficult to identify. For this reason, it is important to use tools that support vulnerability detection.
In order to identify vulnerabilities, it is necessary to perform an analysis of the developed system itself. Currently, there are several techniques that are useful in vulnerability detection.
These techniques can be divided into two: those using static analysis, i.e. using vulnerability detection techniques, and those using dynamic analysis. The fundamental difference between these types of analysis is that the static analysis is performed on the source code of the programme without being executed, while the dynamic analysis observes the execution of the programme, its functionality and the responses it provides. In this case, we are going to focus our attention on the latter type of detection technique, i.e. dynamic analysis.
Vulnerability detection with Fuzzing
The technique of vulnerability detection by fuzzing consists of performing multiple recurring tests. Different random or unexpected parameters on the inputs of a system will be used for these tests. With them we can jeopardise the correct functioning of the service to be analysed.
When making these requests, we try to obtain responses or exceptions that are not contemplated in the programme itself. One of the advantages of this technique is that it can be applied to both software and hardware systems.
The fuzzing technique can be used in two ways. One is in an offensive way, where a third party intends to attack the system. The other way is in defensive mode, in which it is the developer himself who uses this technique to be able to solve the possible vulnerabilities of his program.
Fuzzing Tool
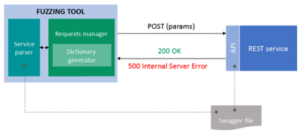
Gradiant, in participation with the BIECO project, has developed a tool called Fuzzing tool. This tool applies the fuzzing technique to detect vulnerabilities. In this case, the tool will analyse a web service that exposes a REST API.
For the development of this tool, a swagger file is used as an input parameter. This file describes the inputs it allows along with their functionalities and parameters. In addition, it also describes the types of response for each of the requests made to the web service. Once the tool has this file, it launches several requests with different parameters described in the swagger file. These parameters are obtained from a large set of data or libraries. They include those that can jeopardise the security or the correct flow of the program. The generated requests are combinations of these parameters that are sent to the web service. After sending them, the tool analyses the responses obtained.
Exhaustive check
Gradiant’s tool checks requests that have not been contemplated in the initial swagger file and stores conflicting requests together with their respective input parameters. In this way, when a developer runs this tool on his web service, he can get information about cases that have not been considered by means of unexpected responses. These responses are the ones provided by the tool.
Thanks to the use of fuzzing techniques, it is possible to detect vulnerabilities and weaknesses in a system that were not considered at an early stage of development. The Fuzzing tool developed by Gradiant will allow the programmer to detect new flaws. Thus, he will be able to focus his efforts on solving the corresponding vulnerabilities detected. This will prevent any attacker from being able to obtain confidential information or perform unintended functions. This is a considerable improvement in ensuring the security of an organisation.

This work was supported by the BIECO project (www.bieco.org) which received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No. 952702.